What is a Browser Hijacker? How It Works & How to Remove It

Browser hiJackers are a Form of malware that assaults and hijacks net browsers. They take the form of malicious browser add-ons or plugins. The risk actors Attack browsers so that they have got as large a target to goal for as feasible. By hijacking browsers and not Operating Systems, the hazard actors don’t need to put in writing a Model in their malware for the Windows, Linux, and Mac sySTEMs.
Regardless of the sort of Computer you operate, you’ll nevertheless use a browser. Attacking browsers shall we the hazard actors produce what's effectively Platform-agnostic malware.
You can seize a browser hijacker from a malicious attachment on an e mail, Downloading inFlamed documents, journeying a Website this is designed to contaminate site visitors, or journeying a valid website that has been compromised by the chance actors in order that it dispenses their browser hijacker.
Browser hijackers Override your browser’s settings to excHange its behavior. You might also see a new Home Page, a brand new Toolbar, or a change for your default Search Engine. These changes will placed false entries in Internet seek consequences and redirect (via a redirect Virus) you to particular websites. The hijackers every so often Make adjustments to your Laptop’s registry in order that the hijackers are hard to Cast off.
The owners of web sites pay the malware authors a small quantity in line with tourist, in a similar way to Spyware. The hijacker authors try and do what they are able to to herd internet site visitors to the web sites a good way to pay them. The websites may also comprise material that is fraudulent, indecent, or which can infect you with malware.
How Hijackers Affect Your Computer
Once the browser hijacker has set up itself on your browser, it's going to use a few or all of these Methods to defend itself and manipulate your browser.
Modifying Your Browser’s Behavior
A browser hijacker might exchange the advent of your browser, the behavior of your browser, or each. Visual signs and symptoms would possibly encompass:
- A new home page
- A new default seek Engine
- A new toolbar
- A bizarre website when you create a brand new tab
- New favorites or Bookmarks and antique bookmarks may be removed
Behavioral Modifications can include:
- A lot of popup adverts
- Bogus entries in your seek effects
- Legitimate websites can’t be reached, specially web sites owned by using antivirus and antimalware agencies
- A drop in browser overall performance
These changes are intended to force you to particular websites and to save you you from achieving web sites that can offer assistance or recommendation in casting off the hijackers.
Data Collection
Browser hijackers music your Surfing behavior and collect Keystrokes. The statistics is sent to the hazard actors. The type of facts a hijacker can accumulate about you includes:
- Search terms you have used
- Websites that you have visited
- Which Files you've got Uploaded, and to which web sites
- Which files you have downloaded, and from where
- Sensitive Records such as login Credentials and credit card details
The gathered facts is either utilized by the risk actors to perpetrate idEntity robbery and fraud, or it may be bought to other criminals.
Digging in Deep
Browser hijackers don’t make it smooth to be able to cast off them. They don’t have an Uninstall alternative, as an Instance. They can use registry Hacks and different endurance tricks to make certain they're very hard to take away.
Some of them will have installed small helper Packages or browser helper items that will reinstall the hijacker if it's far removed.
Performance Loss
Many browser hijackers are quite poorly engineered by way of the risk actors who write them. They don’t care in the Event that they introduce a stress in your browser and decrease its overall performance. Because they don’t care, they don’t try and engineer ways around the difficulty.
They leave their Code as it is, and you have to put up with the degraded overall performance.
Always Keep Your Browser UPDATEd
Make sure you update your browser frequently to benefit from the safety Upgrades each new release has. Google Chrome and Firefox are up to date around each forty to 50 days. Microsoft Edge is up to date with Windows on an approximate six-week cycle. So all the massive three browsers have a comparable update cycle.
How To Remove Browser Hijackers
So you obtain hit and want to know a way to do away with a browser hijacker. Browser hijacker elimination may be as easy as resetting your browser to a clean kingdom, but try contacting a expert or the usage of an Anti-Malware Device first. Here’s what you want to recognise.
- If you have an IT Branch or help crew, you could name on, achieve this, and let them take care of it.
- If you have an anti-malware tool installed as a part of your endpoint safety, attempt walking a scan with that device. That might take away the hijacker for you.
- If the hijacker remains gift after the scan, an internet search –done on a extraordinary computer – would possibly return a specific elimination tool for the version of the browser hijacker which you have been inflamed with. If you find one, handiest consider it if it's miles produced and to be had for down load from a good security Web Page, inclusive of a huge-name antivirus corporation. Posing as a benign malware-removal device is a famous ploy used to unfold malware.
- If you have to, you could try manually casting off the hijacker through hand. You can restore a Current browser to its “Clean Install” kingdom.
Resetting Chrome
To Dispose of a browser hijacker from Chrome, replica and paste this Line Into the deal with bar:
When you press “Enter,” you'll see the “Reset Settings” dialog Field.
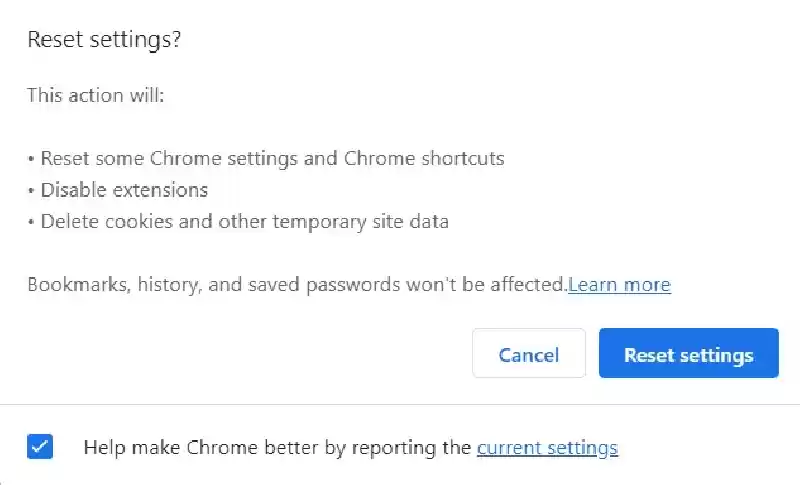
Click the blue “Reset Settings” button to restore Chrome to its authentic settings.
Resetting Firefox
To reset Mozilla Firefox, reproduction and paste the subsequent line into the Address Bar:
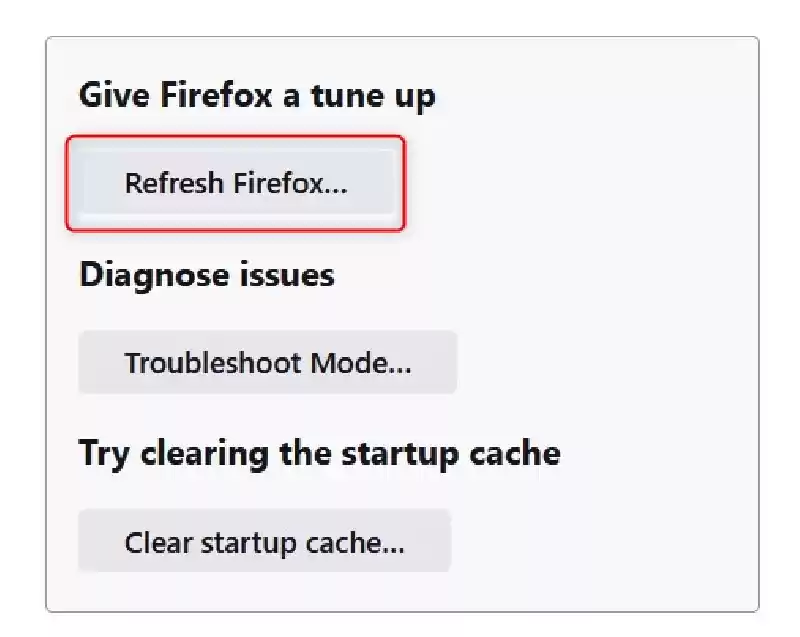
When you press “Enter,” you will see the “Troubleshooting Information” web page. In the top-proper nook, you’ll see the “Give Firefox a song-up” pane.
Click the gray “Refresh Firefox” to reset the browser settings.
Resetting Microsoft Edge
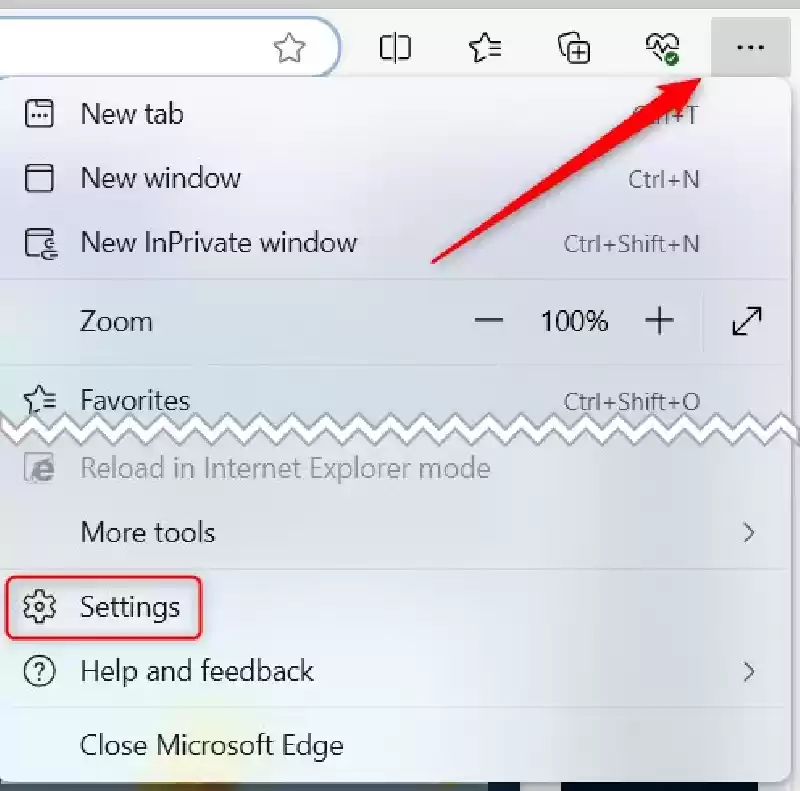
To reset Microsoft Edge, click on the three-dot Menu Icon “…” and choose “Settings” from the Drop-Down Menu.
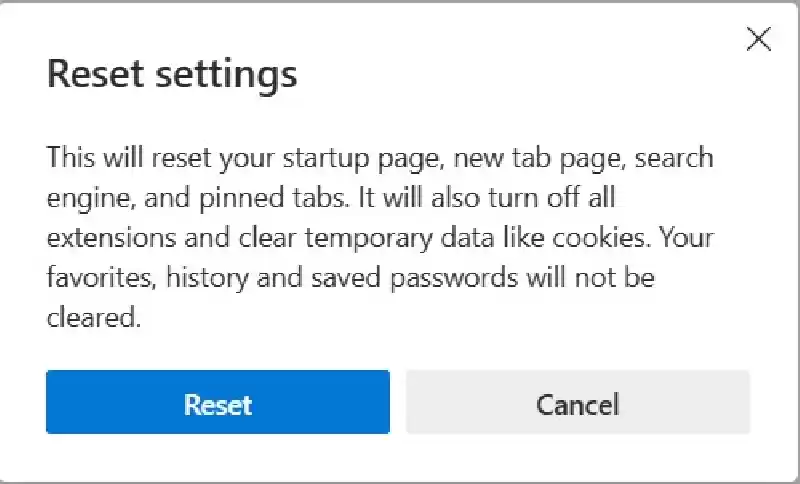
Select the “Reset Settings” choice from the left-hand pane.
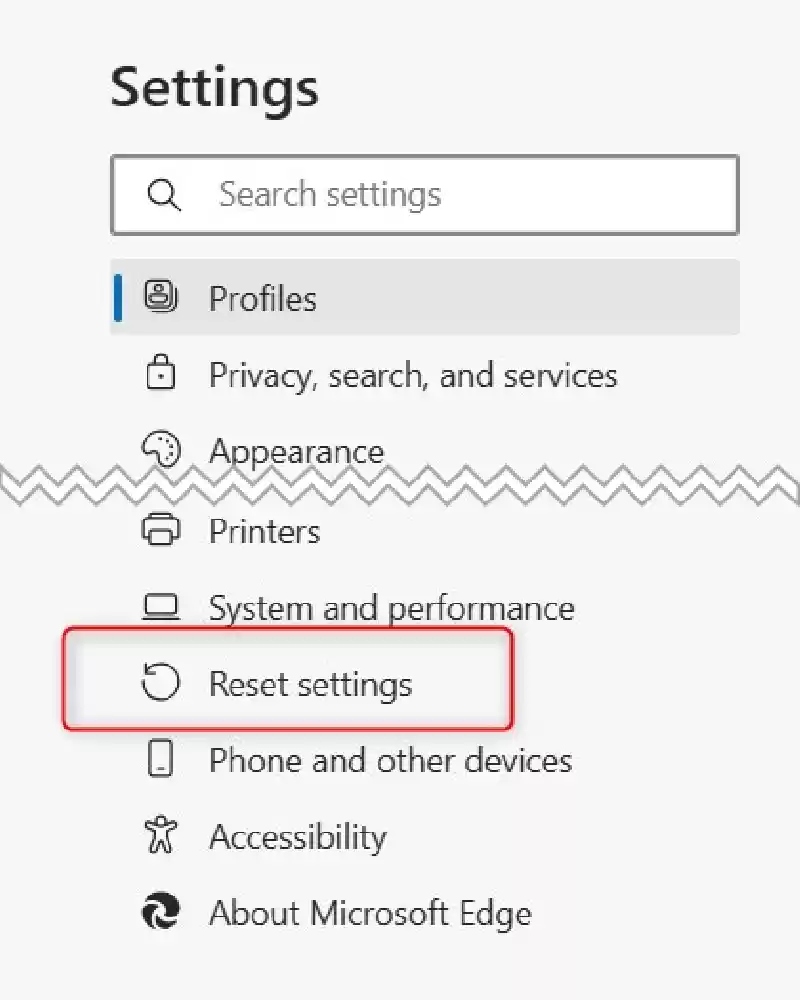
The “Reset Settings” dialog will seem. Click the blue “Reset” button.
Your browser settings can be restored to their default settings.
Resetting Mobile Devices
If the infected tool is a Tablet, telephone, or Chromebook that stores all of its information in the Cloud, it is probably less complicated to manufacturing uNit reset your tool after which download your information from the cloud.
Prevention is Better Than the Cure
- Obey any warnings that your browser would possibly show approximately websites that you’re seeking to visit. If they say the web page is suspicious or insecure, you probably don’t need to proceed to that internet site.
- Don’t download documents or Software from anywhere aside from legitimate web sites.
- Check the small print in the phrases and conditions when you deploy software, and ensure you’re no longer agreeing to permit it to install “other Software Program sometimes” or equally vaguely worded clauses.
- When you’re putting in software, examine every web page of the set up routine cautiously. Don’t just click “Next, Next, Next” to go through the technique as rapid as feasible. Make certain you don’t inadvertently give permission for additonal toolbars and other software program.
- Consider using a JavaScript Blocker. The Chrome ScriptBLock Extension and the Firefox NoScript Security Suite each block JavaScript but let you allow JavaScript temporarily, at your discretion, with a single click on.
- Do a Chunk of studies earlier than installing a browser upload-on or extension. How many customers does it have, whilst was it ultimate updated, and what do the opinions say? If you do a web search on their name, do you notice any disturbing or negative Comments?
Your Score to Browser Hijacker article
Score: 5 out of 5 (1 voters)
Be the first to comment on the Browser Hijacker